Would Happen If Your Business Faced a Catastrophic Event?
Imagine walking into your office one morning only to find that your entire IT infrastructure has been locked down by ransomware. Critical customer data, financial records, and business operations are completely inaccessible. Alternatively, a natural disaster could wipe out your data center, leaving your company in complete disarray. The ability to recover quickly from such scenarios determines whether a business survives or collapses. Yet, not all recovery strategies are created equal.
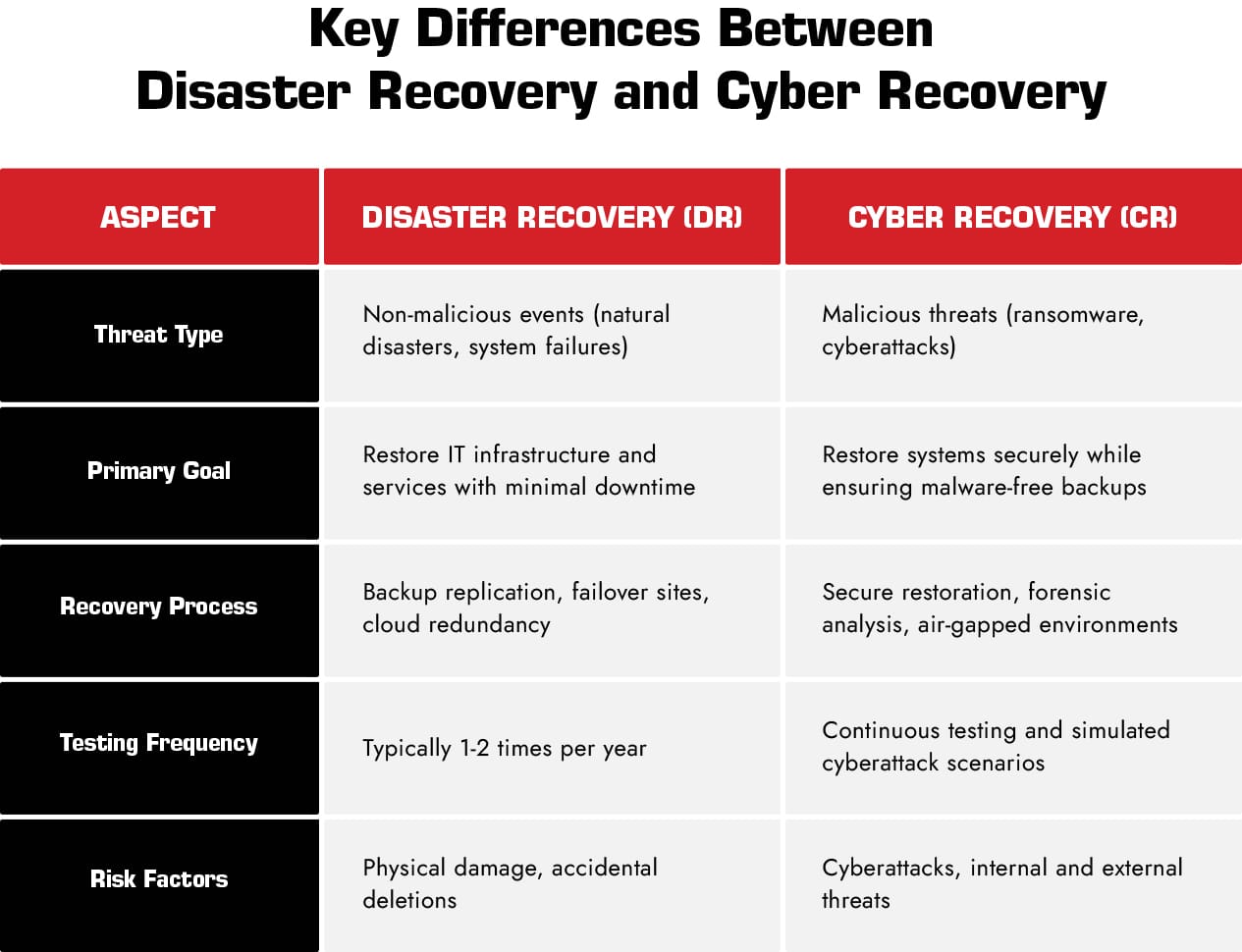
Many organizations mistakenly believe that Disaster Recovery (DR) and Cyber Recovery (CR) are interchangeable. While both play a crucial role in restoring business operations, they are designed to address different threats and require distinct strategies. As cyber threats become increasingly sophisticated and environmental risks grow more unpredictable, companies must understand these distinctions to build a truly resilient recovery plan.
Understanding Disaster Recovery (DR)
Disaster Recovery (DR) focuses on restoring IT systems, infrastructure, and data following non-malicious disruptions, such as:
- Power outages that can compromise system functionality
- Accidental data deletions caused by human error
- Natural disasters (hurricanes, earthquakes, floods)
- Hardware or software failures
The goal of DR is to minimize downtime and ensure business continuity by maintaining redundant backups, failover solutions, and replication mechanisms. Common DR solutions include:
- Off-site data storage and backups to safeguard information
- Cloud-based redundancy solutions for scalable and flexible recovery options
- Business Continuity Planning (BCP) to facilitate rapid recovery and seamless operations
- Access to temporary replacement equipment through an MSP to sustain critical functions during disruptions
Companies that implement DR plans regularly conduct disaster recovery tests—typically once or twice a year—to ensure their ability to restore systems efficiently within an acceptable Recovery Time Objective (RTO).
Understanding Cyber Recovery (CR)
Cyber Recovery (CR) is specifically designed to counter malicious cyber threats, including:
- Ransomware and malware attacks targeting sensitive business data
- Data breaches and insider threats that expose or compromise confidential information
- Distributed Denial-of-Service (DDoS) attacks that can take down critical business applications
- Advanced Persistent Threats (APT) in which attackers infiltrate systems undetected for extended periods
Unlike DR, which assumes backups remain intact, CR necessitates a higher level of security to ensure restored systems are free from malware and reinfections. Key elements of CR include:
- Isolated Recovery Environments (IREs): Air-gapped, secured environments that protect data from cyber threats
- Forensic Data Integrity Validation: Advanced tools that verify the integrity of backups before restoration
- AI-Driven Anomaly Detection: Machine learning systems that detect and mitigate threats before they escalate
Given the rapidly evolving nature of cyber threats, CR testing is more frequent than DR testing, often involving simulated cyberattacks to assess an organization’s ability to recover securely.
Why Cyber Recovery Has Become a Business Imperative
According to a 2024 IBM study, the average cost of a data breach has reached $4.45 million, marking a 15% increase over the past three years. Meanwhile ransomware attacks have surged by over 300% in the past five years, with small and mid-sized businesses facing the highest risk.
Traditional DR plans are not equipped to handle sophisticated cyber threats, which can infiltrate networks and remain dormant for months before executing large-scale attacks. Without a cyber recovery strategy, organizations risk restoring compromised backups, further exacerbating security vulnerabilities.
Creating a Unified Disaster & Cyber Recovery Strategy
To combat modern threats, businesses must develop a comprehensive resilience plan that incorporates both DR and CR strategies. Here’s how:
1. Implement Air-Gapped, Immutable Backups
Traditional backups are highly vulnerable to ransomware encryption. Air-gapped storage ensures backup data is physically separated from production environments, while immutable backups prevent unauthorized alterations.
2. Automate Incident Response & Recovery
Time is of the essence during a cyber incident. AI-driven automation can accelerate threat detection, contain breaches, and initiate rapid recovery, reducing costly downtime.
3. Regularly Test Recovery Procedures
Organizations should conduct frequent disaster recovery and cyber recovery simulations to identify weak points, refine response strategies, and improve recovery timelines.
4. Adopt a Zero Trust Security Framework
Cyber resilience requires more than just recovery—it demands proactive threat prevention. Implementing a Zero Trust model, coupled with Endpoint Detection and Response (EDR) solutions, significantly enhances protection against cyber threats.
5. Build a Cross-Functional Cyber Resilience Team
A successful recovery strategy hinges on collaboration. Organizations should establish cross-functional teams comprising IT, security, legal, compliance, and executive leadership to ensure rapid decision-making during incidents.
Beyond Recovery—Building a Future-Proof Business
Every day, we help businesses like yours:
- Develop robust disaster and cyber recovery strategies tailored to industry needs
- Safeguard critical data and IT infrastructure from physical and cyber threats
- Deploy cutting-edge recovery solutions that minimize downtime and financial losses
With our 24/7 proactive support and industry-leading recovery planning, you can focus on business growth with confidence.
Let’s discuss how we can enhance your company’s resilience—contact us today.

