You can’t build a business on optimism alone.
Optimism is a valuable trait, especially when building and leading a business. But it’s not enough by itself. To successfully face daily challenges, you must also be aware of potential disruptions and, more importantly, be ready to respond quickly and effectively.
Whether you’re running a small business, a growing company, or a structured organization, today, no one can afford to overlook their IT infrastructure. A solid, well-prepared technology backbone is essential for ensuring continuity, efficiency, and security.
In this article, we outline the key steps to make sure your company isn’t caught off guard when a disruption—whether a technical failure, service outage, or cyberattack—strikes.
1. Resilient IT: A Survival Requirement
Today, every company relies on technology for communication, production, customer service, finance, and basic operations. Since IT has become the nervous system of modern business, even a short outage can cause major disruptions.
When an ERP system goes down, orders halt, data access stops, sales pause, and customer trust erodes. The issue is no longer if something goes wrong but when and how well you’re prepared.
According to the IBM Cost of a Data Breach Report, the average cost of a data breach in the U.S. reached over $9 million. And for small to mid-sized businesses, the consequences can be even more devastating—60% go out of business within six months after a cyberattack.
A resilient IT strategy with monitoring, backups, cybersecurity, and ongoing support helps:
- Prevent issues before they arise.
- Recover quickly from downtime or data loss.
- Ensure uninterrupted operations, even under pressure.
Being prepared is no longer a competitive advantage, it’s a condition for survival.
2. Continuous Monitoring: Catch the Signs Before the Outage
When IT systems are working well, we hardly notice. Backups run silently, servers stay responsive, and networks remain stable. Behind this apparent “magic” is continuous monitoring, detecting weak signals before they become serious problems.
Many disruptions don’t happen suddenly. They start with lagging processes, degrading drives, unstable connections, or suspicious traffic spikes. Early intervention avoids emergency support calls and costly downtime.
Continuous monitoring and DNS filtering don’t just enhance security, they also reduce operational overhead. Businesses that implement DNS protection can experience up to a 40% reduction in support tickets thanks to fewer infections, blocked malicious sites, and faster problem detection.
Silent yet active monitoring with automated alerts isn’t just a best practice, it’s a business enabler offering stability, efficiency, and reduced IT support costs.
3. Backup & Disaster Recovery: The Invisible Safety Net
Even the best-designed systems can’t prevent every mishap: failed updates; power outages; human error; or worse, cyberattacks. What truly matters is how quickly you can recover and how much data you can restore.
Reliable automated backups and a well-tested disaster recovery (DR) plan are crucial. It’s not enough to have copies stored somewhere, you need backups of the various versions across locations (on-premise and cloud), regularly tested restoration processes, and guaranteed recovery times.
In one notable real-world incident, a company experienced a total server outage due to a disaster. Thanks to their proactive disaster recovery plan and cloud-based failover solution, they managed to bring their systems back online within approximately two hours, avoiding a $900,000 loss in revenues, all for a cost of around $50,000 per year for the protection system
A well-configured backup and DR solution isn’t an expense, it’s an investment that can save entire workdays and protect customer trust.
4. Multilayered Cybersecurity: Defending at Every Level
Cybersecurity has become a strategic business priority. As attack surfaces expand—through connected devices, remote users, and outdated software—organizations of all sizes are under constant threat.
A recent Forbes article reported a 132% surge in ransomware attacks in 2024, despite a 35% drop in ransom payments. This spike is attributed to the rise of AI-enhanced phishing and techniques that bypass two-factor authentication. The scale and sophistication of threats are accelerating rapidly.
But the biggest challenge isn’t just withstanding an attack—it’s how fast you can respond and recover when the attacks happen. Companies that integrate AI into their security workflows reduce detection and response times from an average of 168 hours (equivalent to a full week) to just seconds.
A modern, resilient cybersecurity strategy should include:
- Next-generation firewalls and real-time threat detection.
- Granular access control for sensitive data.
- Regular penetration testing to identify vulnerabilities before attackers do.
In a world where a single wrong click can compromise an entire network, cybersecurity is no longer optional—it’s vital for business continuity, brand trust, and long-term resilience.
5. Managed & Scalable Cloud: IT That Grows with You
Initially adopted for storage, the cloud has evolved into a strategic platform for resilience, agility, and growth. It enables secure remote access, real-time collaboration, and operational flexibility wherever your team works.
A managed cloud infrastructure, supported by an MSP, allows businesses to scale resources according to demand and pay for only what they use, avoiding waste and reducing fixed IT costs.
This approach is now central to digital strategy: Gartner estimates that by 2028, cloud will no longer be just a technology option but a strategic necessity to remain competitive. Over 50% of enterprises are expected to use industry-specific cloud platforms by then. Those already migrated report an average 30% IT cost reduction and improved business flexibility.
Cloud today isn’t just where data lives, it’s the foundation of a scalable, resilient IT system that supports your business evolution.
6. One Size Doesn’t Fit All: IT Must Adapt to Your Needs
No two businesses are the same. Effective IT strategies must be tailored to fit operational models, industries, geographic distribution, and internal processes.
- In logistics, systems must support real-time visibility of inventory and shipments.
- In hospitality and restaurants, POS reliability is critical—even a brief downtime can result in revenue loss and frustrated customers.
- For family offices, data security and compliance are paramount, especially for managing sensitive financial information.
- On construction sites or remote operations, stable connectivity and mobile access to digital tools are essential.
An effective MSP doesn’t offer generic solutions. It partners with you to understand your operations and deliver an IT infrastructure that’s functional, flexible, and secure.
And when things go wrong, whether it’s 10 am. or 2 am, having a team ready to respond can be the difference between a full-stop and a fast recovery.
The Real-World Value of Resilient IT
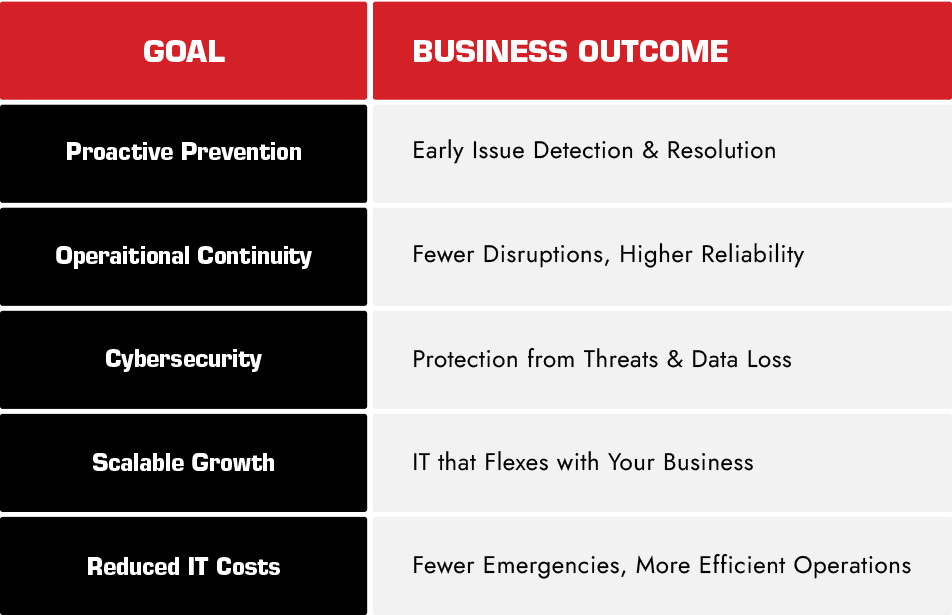
Your Partner in IT Resilience
In a world where every second counts, there’s no room for improvisation.
We support businesses with IT solutions designed to prevent, protect, and empower. Our services include:
- Tailored IT consulting across industries.
- Proactive managed services and 24/7 monitoring.
- Flexible, secure, and scalable cloud infrastructure.
- Multilayered cybersecurity.
- Always-on support, whenever you need it.
Talk to one of our experts and discover how to turn your IT into a driver of efficiency, security, and growth.

